for e-Government

| Open Interfaces for e-Government |
 |
Introduction
Document information
|
Designation |
Introduction to the Austrian Citizen Card |
|
Short name |
Introduction |
|
Version |
1.2.0 |
|
Date |
2004-05-14 |
|
Document class |
Explanation |
|
Document status |
Recommendation |
|
Short description |
This document provides an introduction to the Austrian Citizen Card. |
|
Authors |
Arno Hollosi |
|
Work group |
Federal Chancellery, Federal Staff Unit for ICT Strategy, Technology and Standards |
|
© |
This specification is supplied by A-SIT and the Federal Chancellery. It may be used without modification provided that reference is made to this copyright notice. The specification may be expanded, however any additional material must be clearly identified and the expanded specification must be made freely available. |
Preliminary note: For better readability, this document dispenses with non-gender-specific formulations. However, the formulations expressly relate to both sexes.
The Citizen Card is a model that provides a series of functions for carrying out e-Government and e-Commerce transactions securely. The Citizen Card can in particular be used to create and verify electronic signatures for electronic documents, to encrypt and decrypt electronic documents, to calculate and check hash values for electronic documents, and to record data in a data storage area and retrieve it from there.
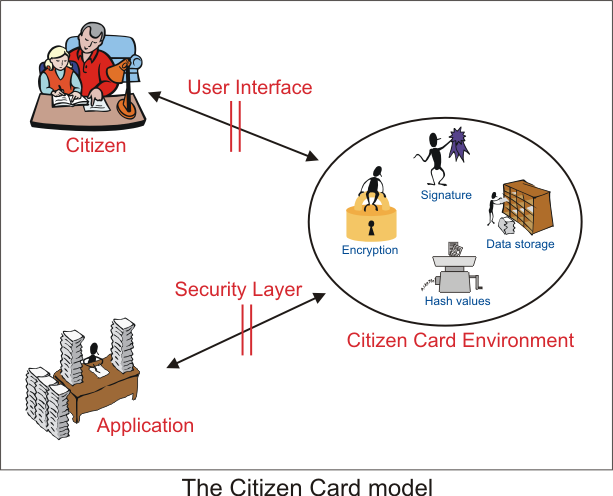
The diagram shows the elements involved when the Citizen Card is used. These are the Citizen Card Environment, which encapsulates the functions described above, the citizen, who uses these functions, and the application, which controls the Citizen Card Environment in such a way that the citizen can use the functions at his convenience.
The diagram also shows two interfaces. These are described in detail in the following specifications: The user interface regulates communication between the citizen and the Citizen Card Environment, while the Security Layer interface defines the interaction between the application and the Citizen Card Environment.
The following glossary describes the interfaces and the elements involved in detail.
This section offers an overview of the various functions provided by the Citizen Card Environment. The functions can largely be divided into four major areas:
The citizen can use the Citizen Card Environment both to sign electronic documents and to verify electronic signatures.
One of the key features of the Citizen Card Environment in both cases is the fact that the citizen can view the actual electronic documents: When creating an electronic signature, he can first verify exactly what data he is actually signing. When verifying an existing signature, the citizen can determine what data is authenticated by the signature.
A Citizen Card Environment offers a secure signature according to the Austrian Signature Act [SigG] or an administrative signature. In e-Government, administrative signatures shall, according to the Austrian E-Government Act [E-GovG], be treated the same way as secure electronic signatures for a transitional period. Thus, for example, the Citizen Card Environment contains the signature creation device which is demanded by law and which requires certification in order to create a secure electronic signature. The advantage of encapsulating the components to be certified into a logical unit is that developers don't have to worry about these legal requirements when designing an application.
The citizen can use the Citizen Card Environment both to encrypt his own electronic documents for any recipients and to decrypt encrypted documents using a decryption key held in the Citizen Card Environment.
The citizen can use the Citizen Card Environment both to calculate a hash value for an electronic document and to verify a hash value for an electronic document.
The Citizen Card Environment provides the citizen with a data storage area for reading and writing data required for e-Government or e-Commerce procedures.
The specifications divide the data storage area into logical units known as info boxes. New info boxes can be created in the data storage area and existing ones can be read, modified and deleted.
The Citizen Card Environment always contains a series of standardised info boxes. This means, for example, that the certificates belonging to the signature and encryption keys held in the Citizen Card Environment can be read out. Info boxes can also be used to access the person identity link and authorisations defined in [E-GovG].
These specifications purposely avoid providing details of the physical location of the storage area data. Several options are conceivable and these could be combined to form a common logical data storage area, e.g.:
Because the info boxes stored in the data storage area may hold sensitive information, the specifications define appropriate requirements for storage and for access protection.
This section provides an overview of the various specification documents relating to the Austrian Citizen Card. All of these are normative documents.
This document. [next...]
This document describes the Security Layer interface which can be used by an application to control the functions provided by the Citizen Card Environment. The interface standardises a series of commands; each command obeys a simple question/answer scheme, i.e. the application issues a query to the Citizen Card Environment and the Citizen Card Environment responds after the command has been processed (and after any interaction with the citizen via the user interface) with the appropriate response to the application. [next...]
This document defines the identifiers for those key boxes and info boxes that are mandatory.
A key box identifies a key held in the Citizen Card Environment that is available for creating electronic signatures and/or decrypting electronic data. The key box identifier in the relevant Security Layer commands defines which key is to be used for creating a signature or decryption.
An info box identifies a dataset stored in the Citizen Card Environment to which read and write access is available with Security Layer commands. The info box identifier is used in these commands to define which dataset is to be created, read, modified or deleted. [next...]
This document defines which Security Layer commands must always be implemented by a Citizen Card Environment. It also contains profiles of the signature formats used by the commands for signature creation, signature verification, encryption and decryption, regulations in relation to the viewer component of the Citizen Card Environment, and requirements for the resolution of the URLs that occur in the various commands. [next...]
The Security Layer interface can be accessed using a variety of transport protocols. This document describes the binding of the Security Layer to the TCP, TLS, HTTP and HTTPS transport protocols. [next...]
The Citizen Card Environment must communicate with the citizen via the user interface in order to complete a number of Security Layer commands, for example displaying the data to be signed when a signature is created and the activation of the signature function by the citizen. This document defines the requirements placed on this user interface for the various commands. [next...]
The execution and result of most Security Layer commands require protection. This means that not every application is permitted to execute every Security Layer command or access the result of command execution. This document specifies access protection that must be observed by a Citizen Card Environment. For this, the authentication of the accessing application is first classified. Starting from this classification, rules are defined that determine whether or not an application may execute a command. [next...]
It is important for the acceptance of the Citizen Card that all Citizen Card Environments available on the market are able to handle at least one common document format in their viewer component (used for example to display the data to be signed when creating a signature). This format should have appropriate options for layout and incorporating images, however should still be suitable in principle as a viewer format for secure signatures. This document specifies just such a document format based on XHTML and CSS2. [next...]
If, for some reason, a command cannot be processed by the Citizen Card Environment, it replies to the application with a specified error response instead of the response belonging to the query. This document specifies the error codes supplied in this error response. [next...]
This document lists known errata in the specifications for the Austrian Citizen Card from version 1.1.0 onwards. When one of the specification documents is published with a higher version number, the errata listed up to this publication date are incorporated in the latest specification, however all errata are still listed in this document. As soon as an erratum has been entered in this document, it is regarded as eliminated in terms of the correction listed in the entry – where applicable. [next...]
This section provides an overview of the other documents relating to the Austrian Citizen Card. These documents contain explanations and are purely informational in character.
This document contains a tutorial for developers of applications. It contains examples for all Security Layer commands as well as multi-level procedures for common application scenarios of the Citizen Card. [next...]
| Date | Version | Changes |
|---|---|---|
| 2004-05-14 | 1.2.0 |
|
| 2002-08-31 | 1.1.0 |
|
| 1.0.0 |
|